Digital signature in cryptography pdf
Contents Contents i Algorithms & Protocols v List of Major Definitions vi Preface vii Numbering and Notation ix 1 Introduction 1 1.1 Classical Cryptography: Hidden Writing . . . . . 1
In the lecture, we briefly mentioned digital signatures as an application of hashing. Now we intro duce digital signatures as a stand-alone primitive.
A digital signature is a secure form of an electronic signature. In this way, digital signatures are a sub-group of In this way, digital signatures are a sub-group of electronic signatures, and they provide signature and content integrity as well as non-repudiation of signed
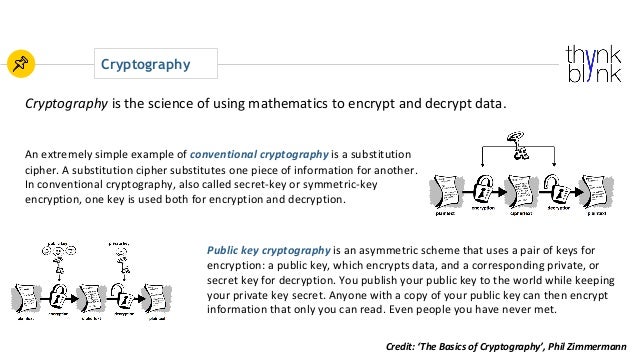
1 Cryptography, digital signature Dr. László Daragó, Ph.D. Outline • Cryptography basics – Symmetric key cryptography – Asymmetric (or public-) key cryptography
A digital watermark and signature method for image authentication using cryptography analysis is proposed. The digital signature created for the original
Providing privacy and authenticity remains a central goal for cryptographic protocols, but the field has expanded to encompass many others, including e-voting, digital coins, and secure auctions. This paper explains what cryptography is about and how we can scientifically justify a …
We will use the Digital Signature (DS) Algorithm as opposed to RSA digital signature algorithm (RSASS) or Elliptic Curve digital signature algorithm (ECDSA). FIPS 186-2 specifies the use of a 1024 bit p , a 160 bit q , and SHA-1 as the hash.
Template:About A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created …
Hi Ravinder, there’s a series dedicated to cryptography and digital signatures on this blog, check out the Security and Cryptography page. Look at the post entitled “Introduction to digital signatures in .NET cryptography” to get you started. //Andras
Cryptography Lecture 8 Digital signatures, hash functions. A Message Authentication Code is what you get from symmetric cryptography A MAC is used to prevent Eve from creating a new message and inserting it instead of Alice’s message Key Key Alice Bob Eve Create MAC Verify MAC. Signature vs MAC A MAC, Message Authentication Code, preserves data integrity, i.e., it ensures that creation …
Digital signatures use Public Key cryptography, which relies on three types of providers to deliver the required technologies and services: solution, technology, and service providers. Solution providers deliver signature platforms and document solutions. Technology providers deliver essential components like authentication technologies, mobile apps, and hardware security modules (HSMs
4.1 Lab on Digital Signature Visualization 1. Select from menu of CrypTool “Digital Signatures/PKI” “Signature Demonstration (Signature
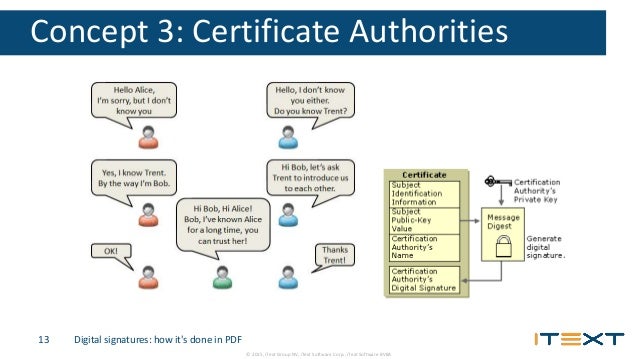
Digital signatures in PDF documents address these needs by providing a way to authenticate digital data based on public k ey cryptography. This document describes how digital signatures are represented in a PDF document. It explains the digital signature security features supported by PDF, and how they solve the need for trusted documents and signatures. This document does not attempt …
The digital signature is the equivalent of the handwritten signature and is intended to solve security problems in the digital communication. The signature is unique to each signer and is widely used to confirm that the document content originated from the signer and has not been modified in any way.
A digital signature should have all the aforementioned features of a conventional signature plus a few more as digital signatures are being used in practical, but sensitive, applications such as secure e-mail and credit card transactions over the Internet. Since a digital signature is just a sequence of zeroes and ones, it is desirable for it to have the following properties: the signature
the digital signature of the CA Once it’s issued, the CA will put the certificate on your hard drive, along with a private key. Once that’s all in place, you’re ready to send certified emails.
In this paper, algorithms for multivariate public key cryptography and digital signature are described. Plain messages and encrypted messages are arrays, consisting of elements from a fixed finite
Elements of applied cryptography Digital Signatures A digital signature is a number dependent on some secret known only to the signer and, additionally, on the content of the message being signed PROPERTY. A digital signature must be verifiable, i.e., if a dispute arises an unbiased third party must be able to solve the dispute equitably, without requiring access to the signer’s secret
International Journal of Computer Applications (0975 – 8887) Volume 117 – No. 16, May 2015 1 Survey on Techniques Developed using Digital Signature: Public key Cryptography
A valuable reference for students, professors, and researchers, Digital Signature Schemes can be used for self-study, as a supplement to a course on theoretical cryptography, or as …
What are the differences between a digital signature a
PKI elliptic curve cryptography and digital signatures
Cryptography: Authentication, Blind Signatures, and Digital Cash∗ Rebecca Bellovin 1 Introduction One of the most exciting ideas in cryptography in the past few decades, with the widest
Public key cryptography (PKC) not only solves this problem gracefully, but also provides enhanced security services such as non-repudiation and digital signatures. To take advantage of PKC, each
The signature is placed in a PDF signature dictionary which contains the name of the signature handler which will be used to process that signature (Figure 3). a smart card. etc.Digital Signatures in a PDF PKI. the signer’s certificate is embedded in the PDF file. and other data. } /Contents • Certificate • Signed message digest • Timestamp %EOF Signature value Acrobat Family of
2 Cryptography • Overview – Symmetric Key Cryptography – Public Key Cryptography – Message integrity and digital signatures References: Stallings

Digital signatures, digital certificates, and advanced electronic signatures are all types of electronic signatures that use cryptography to authenticate the identity of the person signing and to secure their electronic signature. They are all very reliable, but they each have different legal consequences in terms of South African law. Even if you know that you want a very reliable electronic
A digital signature or digital signature scheme is a type of asymmetric cryptography used to simulate the security properties of a handwritten signature on paper.
Digital signatures are used to detect unauthorized modifications to data and to authenticate the identity of the signatory. In addition, the recipient of signed data can use a digital signature as evidence in demonstrating to a third party that the signature was, in fact, generated by the claimed signatory. This is known as non-repudiation, since the signatory cannot easily repudiate the
CRYPTOGRAPHY AND DIGITAL SIGNATURE ISSUES Presented by Robert T. J. Bond Solicitor and Notary Public Hobson Audley Hopkins & Wood Solicitors 7 Pilgrim Street
In cryptography, the Elliptic Curve Digital Signature Algorithm (ECDSA) offers a variant of the Digital Signature Algorithm (DSA) which uses elliptic curve cryptography.

Non-repudiation + integrity A’s digital signature of a cryptographic hash of message m guarantees that m was signed by A and that m was not altered. Anybody can computer the hash of m; anybody can verify A’s signature. Or conceptually more complex Message Authentication Code (MAC)
digital signatures could be the major application of cryptography in the years to come.Chapter 1 Introdtion We use the term signer for an entity who creates a digital signature. 2 .2 OBJECIVES • To define a digital signature • To define security services provided by a digital signature • To define attacks on digital signatures • To discuss some digital signature schemes. 1. including
Digital signatures employ asymmetric cryptography. In many instances they provide a layer of validation and security to messages sent through a non-secure channel: Properly implemented, a digital signature gives the receiver reason to believe the message was sent by the claimed sender. Digital seals and signatures are equivalent to handwritten signatures and stamped seals. Digital signatures
1 A digital signature is the term used for marking or signing an electronic document, by a process meant to be equivalent to paper signatures, but which makes use of a technology known as public-key cryptography.
A digital signature is an authentication mechanism that enables the creator of the message to attach a code that act as a signature. It is formed by taking the hash of message and encrypting the message with creator’s private key.
A digital signature is a term used to describe a data string which associates a digital message with an assigned person only. Therefore, the main goal (or contribution) of this work is to study a
Digital signatures require both hashing and asymmetric cryptography. I can edit if there is a point where the answer is ambiguous or uses the wrong term. I can edit if there is a point where the answer is ambiguous or uses the wrong term.
A (digital) signature is created with a private key, and verified with the corresponding public key of an asymmetric key-pair. Only the holder of the private key can create this signature, and normally anyone knowing the public key can verify it. Digital signatures don’t …
Cryptographic Interoperability Digital Signatures
An Efficient Implementation of Digital Signature Algorithm with SRNN Public Key Cryptography *Mr. Hemant Kumar, **Dr. Ajit Singh **Asst. Professor, Computer Science & Engineering Dept., Kumaon Engineering College, Uttarakhand, India _____ ABSTRACT Digital Signature schemes are mostly used in cryptographic protocols to provide services like entity authentication, authenticated key transport …
Digital signatures rely on the ability of a public-key signing algorithm to sign a message—to generate a signature from the message with a private key. Later, anyone with that signature can verify the message using the corresponding public key. (This uses the keys in the opposite order as public-key encryption and public-key decryption to provide confidentiality—encryption with a public
A digital signature or digital signature scheme is a type of asymmetric cryptography. For messages sent through an insecure channel, a good implementation of digital signature algorithm is the one that makes the receiver believe that the message was sent by the claimed sender, and trust the message. – digital automatic voltage regulator pdf
A_Seminar_Report_On_DIGITAL_SIGNATURE_AL.pdf Public Key
Introduction to digital signatures in .NET cryptography

Digital Signature Public Key Cryptography Scribd
An Efficient Implementation of Digital Signature Algorithm
Digital Signature Public Key Cryptography Cryptography
Digital Signatures Public Key Cryptography Scribd


[PDF] Cryptography & Digital Signatures Free Download PDF
https://en.m.wikipedia.org/wiki/Book:Cryptography
Cryptography More Primitives 1 Digital Signatures
– Digital Signature Standard (DSS) State of California
Digital Signature and Watermark Methods For Image

Cryptography & digital signature facultymembers.sbu.ac.ir
Electronic signatures and cryptography Michalsons
Introduction to digital signatures in .NET cryptography
Multivariate Public Key Cryptography and Digital Signature
2 Cryptography • Overview – Symmetric Key Cryptography – Public Key Cryptography – Message integrity and digital signatures References: Stallings
Non-repudiation integrity A’s digital signature of a cryptographic hash of message m guarantees that m was signed by A and that m was not altered. Anybody can computer the hash of m; anybody can verify A’s signature. Or conceptually more complex Message Authentication Code (MAC)
A valuable reference for students, professors, and researchers, Digital Signature Schemes can be used for self-study, as a supplement to a course on theoretical cryptography, or as …
Public key cryptography (PKC) not only solves this problem gracefully, but also provides enhanced security services such as non-repudiation and digital signatures. To take advantage of PKC, each
4.1 Lab on Digital Signature Visualization 1. Select from menu of CrypTool “Digital Signatures/PKI” “Signature Demonstration (Signature
What are the differences between a digital signature a
PKI elliptic curve cryptography and digital signatures
Contents Contents i Algorithms & Protocols v List of Major Definitions vi Preface vii Numbering and Notation ix 1 Introduction 1 1.1 Classical Cryptography: Hidden Writing . . . . . 1
Digital signatures, digital certificates, and advanced electronic signatures are all types of electronic signatures that use cryptography to authenticate the identity of the person signing and to secure their electronic signature. They are all very reliable, but they each have different legal consequences in terms of South African law. Even if you know that you want a very reliable electronic
International Journal of Computer Applications (0975 – 8887) Volume 117 – No. 16, May 2015 1 Survey on Techniques Developed using Digital Signature: Public key Cryptography
A digital signature or digital signature scheme is a type of asymmetric cryptography used to simulate the security properties of a handwritten signature on paper.
A digital watermark and signature method for image authentication using cryptography analysis is proposed. The digital signature created for the original
In cryptography, the Elliptic Curve Digital Signature Algorithm (ECDSA) offers a variant of the Digital Signature Algorithm (DSA) which uses elliptic curve cryptography.
Public key cryptography (PKC) not only solves this problem gracefully, but also provides enhanced security services such as non-repudiation and digital signatures. To take advantage of PKC, each
Digital signatures in PDF documents address these needs by providing a way to authenticate digital data based on public k ey cryptography. This document describes how digital signatures are represented in a PDF document. It explains the digital signature security features supported by PDF, and how they solve the need for trusted documents and signatures. This document does not attempt …
Cryptography: Authentication, Blind Signatures, and Digital Cash∗ Rebecca Bellovin 1 Introduction One of the most exciting ideas in cryptography in the past few decades, with the widest
Elements of applied cryptography Digital Signatures A digital signature is a number dependent on some secret known only to the signer and, additionally, on the content of the message being signed PROPERTY. A digital signature must be verifiable, i.e., if a dispute arises an unbiased third party must be able to solve the dispute equitably, without requiring access to the signer’s secret
the digital signature of the CA Once it’s issued, the CA will put the certificate on your hard drive, along with a private key. Once that’s all in place, you’re ready to send certified emails.
Digital signatures employ asymmetric cryptography. In many instances they provide a layer of validation and security to messages sent through a non-secure channel: Properly implemented, a digital signature gives the receiver reason to believe the message was sent by the claimed sender. Digital seals and signatures are equivalent to handwritten signatures and stamped seals. Digital signatures
A digital signature is a term used to describe a data string which associates a digital message with an assigned person only. Therefore, the main goal (or contribution) of this work is to study a
Digital Signatures Public Key Cryptography Scribd
Digital Signatures Jonathan Katz Springer
Digital signatures use Public Key cryptography, which relies on three types of providers to deliver the required technologies and services: solution, technology, and service providers. Solution providers deliver signature platforms and document solutions. Technology providers deliver essential components like authentication technologies, mobile apps, and hardware security modules (HSMs
Digital signatures rely on the ability of a public-key signing algorithm to sign a message—to generate a signature from the message with a private key. Later, anyone with that signature can verify the message using the corresponding public key. (This uses the keys in the opposite order as public-key encryption and public-key decryption to provide confidentiality—encryption with a public
2 Cryptography • Overview – Symmetric Key Cryptography – Public Key Cryptography – Message integrity and digital signatures References: Stallings
Elements of applied cryptography Digital Signatures A digital signature is a number dependent on some secret known only to the signer and, additionally, on the content of the message being signed PROPERTY. A digital signature must be verifiable, i.e., if a dispute arises an unbiased third party must be able to solve the dispute equitably, without requiring access to the signer’s secret
Public key cryptography (PKC) not only solves this problem gracefully, but also provides enhanced security services such as non-repudiation and digital signatures. To take advantage of PKC, each
Contents Contents i Algorithms & Protocols v List of Major Definitions vi Preface vii Numbering and Notation ix 1 Introduction 1 1.1 Classical Cryptography: Hidden Writing . . . . . 1
1 A digital signature is the term used for marking or signing an electronic document, by a process meant to be equivalent to paper signatures, but which makes use of a technology known as public-key cryptography.
Digital signatures are used to detect unauthorized modifications to data and to authenticate the identity of the signatory. In addition, the recipient of signed data can use a digital signature as evidence in demonstrating to a third party that the signature was, in fact, generated by the claimed signatory. This is known as non-repudiation, since the signatory cannot easily repudiate the
In the lecture, we briefly mentioned digital signatures as an application of hashing. Now we intro duce digital signatures as a stand-alone primitive.
Cryptography: Authentication, Blind Signatures, and Digital Cash∗ Rebecca Bellovin 1 Introduction One of the most exciting ideas in cryptography in the past few decades, with the widest
Hi Ravinder, there’s a series dedicated to cryptography and digital signatures on this blog, check out the Security and Cryptography page. Look at the post entitled “Introduction to digital signatures in .NET cryptography” to get you started. //Andras
1 Cryptography, digital signature Dr. László Daragó, Ph.D. Outline • Cryptography basics – Symmetric key cryptography – Asymmetric (or public-) key cryptography
4.1 Lab on Digital Signature Visualization 1. Select from menu of CrypTool “Digital Signatures/PKI” “Signature Demonstration (Signature
Digital Signature Public Key Cryptography Cryptography
Survey on Techniques Developed using Digital Signature
A digital signature or digital signature scheme is a type of asymmetric cryptography used to simulate the security properties of a handwritten signature on paper.
The digital signature is the equivalent of the handwritten signature and is intended to solve security problems in the digital communication. The signature is unique to each signer and is widely used to confirm that the document content originated from the signer and has not been modified in any way.
Cryptography Lecture 8 Digital signatures, hash functions. A Message Authentication Code is what you get from symmetric cryptography A MAC is used to prevent Eve from creating a new message and inserting it instead of Alice’s message Key Key Alice Bob Eve Create MAC Verify MAC. Signature vs MAC A MAC, Message Authentication Code, preserves data integrity, i.e., it ensures that creation …
A digital signature is an authentication mechanism that enables the creator of the message to attach a code that act as a signature. It is formed by taking the hash of message and encrypting the message with creator’s private key.
Contents Contents i Algorithms & Protocols v List of Major Definitions vi Preface vii Numbering and Notation ix 1 Introduction 1 1.1 Classical Cryptography: Hidden Writing . . . . . 1
4.1 Lab on Digital Signature Visualization 1. Select from menu of CrypTool “Digital Signatures/PKI” “Signature Demonstration (Signature
1 A digital signature is the term used for marking or signing an electronic document, by a process meant to be equivalent to paper signatures, but which makes use of a technology known as public-key cryptography.
In cryptography, the Elliptic Curve Digital Signature Algorithm (ECDSA) offers a variant of the Digital Signature Algorithm (DSA) which uses elliptic curve cryptography.
Providing privacy and authenticity remains a central goal for cryptographic protocols, but the field has expanded to encompass many others, including e-voting, digital coins, and secure auctions. This paper explains what cryptography is about and how we can scientifically justify a …
Digital signatures use Public Key cryptography, which relies on three types of providers to deliver the required technologies and services: solution, technology, and service providers. Solution providers deliver signature platforms and document solutions. Technology providers deliver essential components like authentication technologies, mobile apps, and hardware security modules (HSMs
An Efficient Implementation of Digital Signature Algorithm
Cryptography in .NET Digital Signatures – Stephen Haunts
Providing privacy and authenticity remains a central goal for cryptographic protocols, but the field has expanded to encompass many others, including e-voting, digital coins, and secure auctions. This paper explains what cryptography is about and how we can scientifically justify a …
A digital signature is a term used to describe a data string which associates a digital message with an assigned person only. Therefore, the main goal (or contribution) of this work is to study a
digital signatures could be the major application of cryptography in the years to come.Chapter 1 Introdtion We use the term signer for an entity who creates a digital signature. 2 .2 OBJECIVES • To define a digital signature • To define security services provided by a digital signature • To define attacks on digital signatures • To discuss some digital signature schemes. 1. including
Digital signatures employ asymmetric cryptography. In many instances they provide a layer of validation and security to messages sent through a non-secure channel: Properly implemented, a digital signature gives the receiver reason to believe the message was sent by the claimed sender. Digital seals and signatures are equivalent to handwritten signatures and stamped seals. Digital signatures
A digital signature or digital signature scheme is a type of asymmetric cryptography. For messages sent through an insecure channel, a good implementation of digital signature algorithm is the one that makes the receiver believe that the message was sent by the claimed sender, and trust the message.
The signature is placed in a PDF signature dictionary which contains the name of the signature handler which will be used to process that signature (Figure 3). a smart card. etc.Digital Signatures in a PDF PKI. the signer’s certificate is embedded in the PDF file. and other data. } /Contents • Certificate • Signed message digest • Timestamp %EOF Signature value Acrobat Family of
Digital signatures, digital certificates, and advanced electronic signatures are all types of electronic signatures that use cryptography to authenticate the identity of the person signing and to secure their electronic signature. They are all very reliable, but they each have different legal consequences in terms of South African law. Even if you know that you want a very reliable electronic
A digital signature or digital signature scheme is a type of asymmetric cryptography used to simulate the security properties of a handwritten signature on paper.
CRYPTOGRAPHY AND DIGITAL SIGNATURE ISSUES Presented by Robert T. J. Bond Solicitor and Notary Public Hobson Audley Hopkins & Wood Solicitors 7 Pilgrim Street
Hi Ravinder, there’s a series dedicated to cryptography and digital signatures on this blog, check out the Security and Cryptography page. Look at the post entitled “Introduction to digital signatures in .NET cryptography” to get you started. //Andras
1 Cryptography, digital signature Dr. László Daragó, Ph.D. Outline • Cryptography basics – Symmetric key cryptography – Asymmetric (or public-) key cryptography
Contents Contents i Algorithms & Protocols v List of Major Definitions vi Preface vii Numbering and Notation ix 1 Introduction 1 1.1 Classical Cryptography: Hidden Writing . . . . . 1
Digital signatures rely on the ability of a public-key signing algorithm to sign a message—to generate a signature from the message with a private key. Later, anyone with that signature can verify the message using the corresponding public key. (This uses the keys in the opposite order as public-key encryption and public-key decryption to provide confidentiality—encryption with a public
Digital signatures are used to detect unauthorized modifications to data and to authenticate the identity of the signatory. In addition, the recipient of signed data can use a digital signature as evidence in demonstrating to a third party that the signature was, in fact, generated by the claimed signatory. This is known as non-repudiation, since the signatory cannot easily repudiate the
A digital signature is a secure form of an electronic signature. In this way, digital signatures are a sub-group of In this way, digital signatures are a sub-group of electronic signatures, and they provide signature and content integrity as well as non-repudiation of signed

Digital signatures rely on the ability of a public-key signing algorithm to sign a message—to generate a signature from the message with a private key. Later, anyone with that signature can verify the message using the corresponding public key. (This uses the keys in the opposite order as public-key encryption and public-key decryption to provide confidentiality—encryption with a public
Digital Signature Public Key Cryptography Scribd